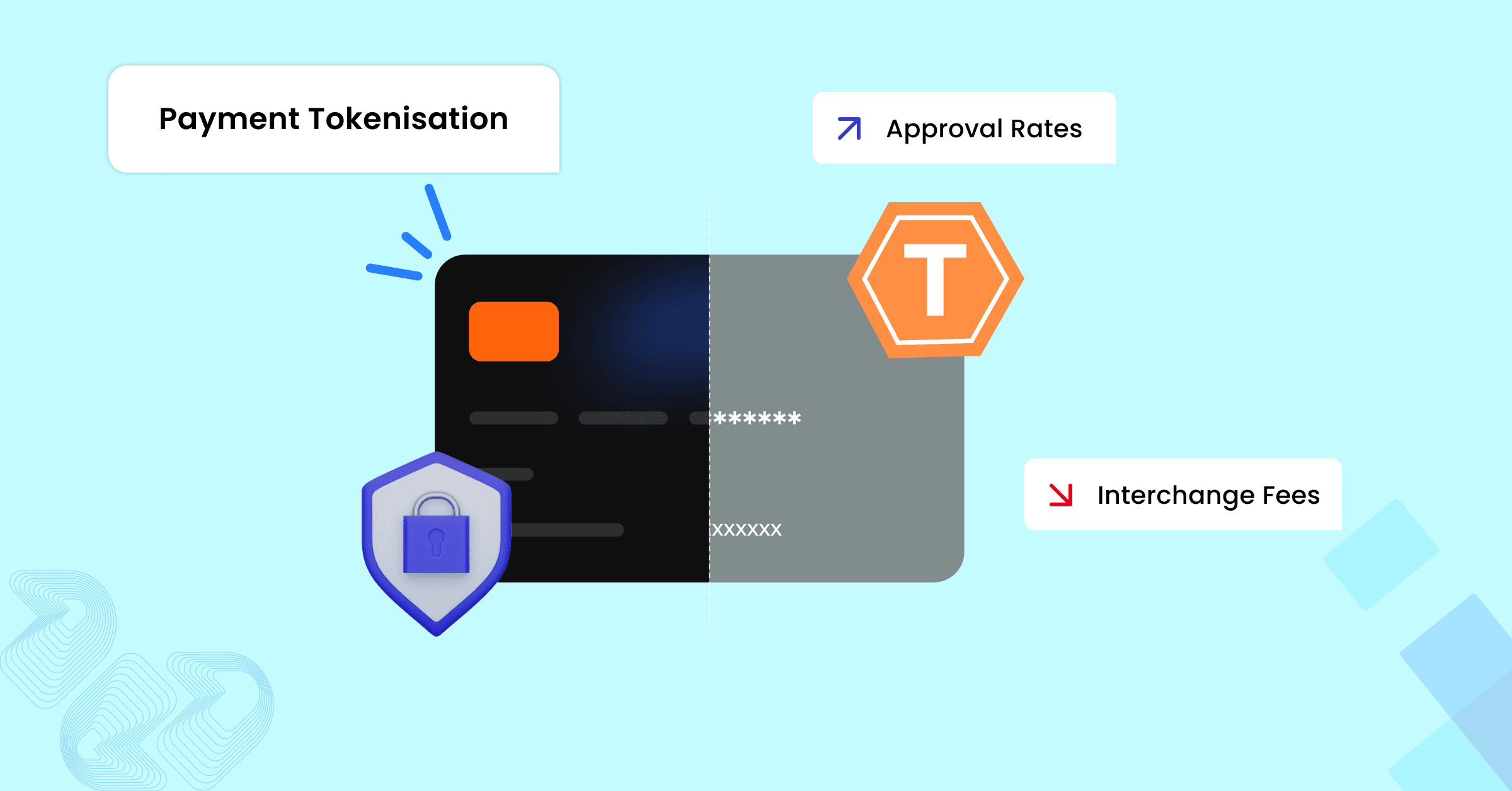
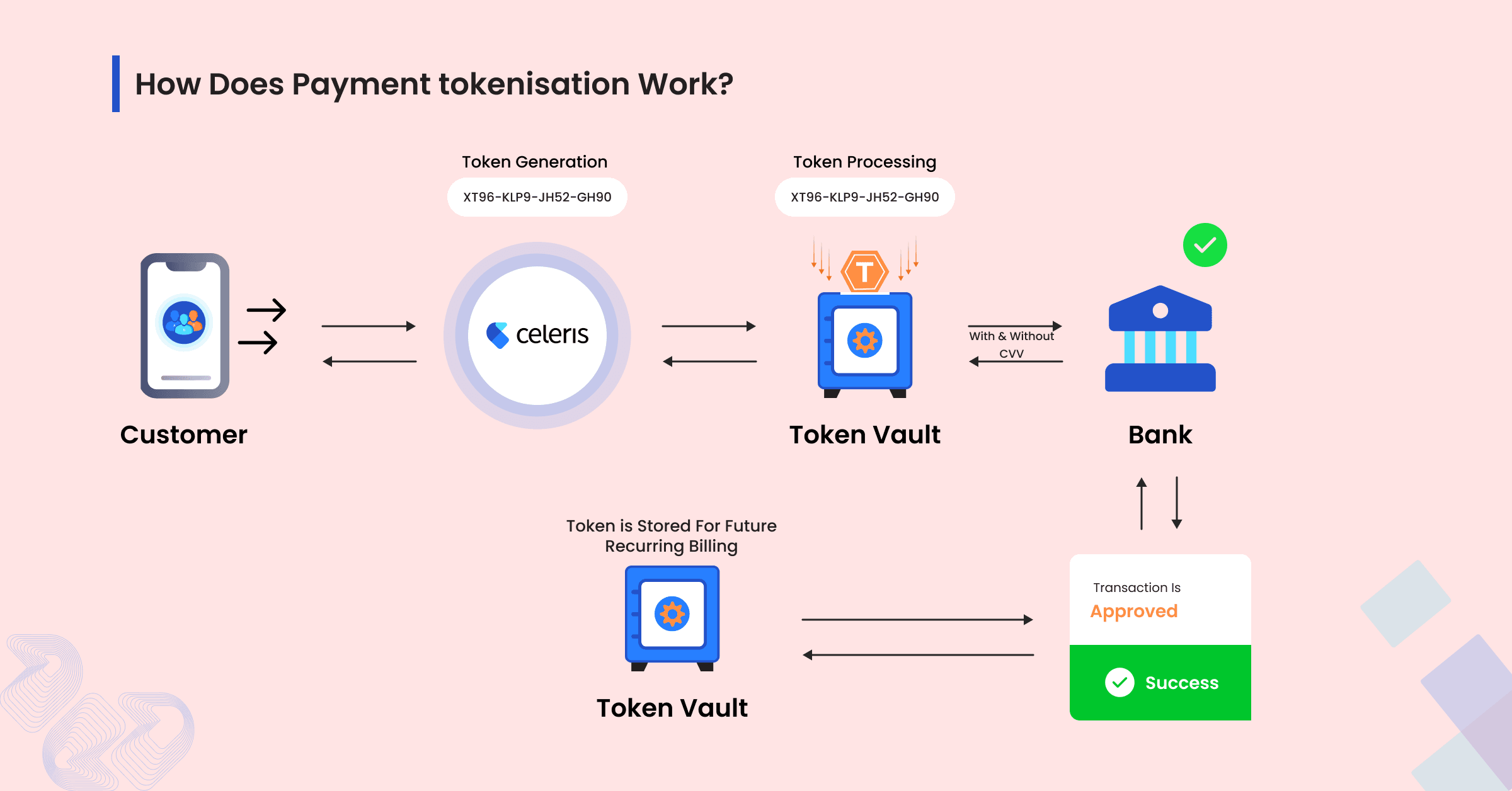
Here’s a simplified breakdown of the payment tokenization process:
-
Initiating a Transaction: A customer enters their card details at checkout or taps their card on a payment terminal.
-
Token Generation: A tokenisation service provider, such as Celeris, captures the real card details and generates a unique token to replace them. For example, the card number “4512-1243-5678-8765” becomes “XT96-KLP9-JH52-GH90.”
-
Token Storage in Secure Vault: The newly generated token is stored in a secure token vault managed by the provider, while the actual card details are isolated.
-
Verifying the Transaction The token is sent through the payment gateway to the issuer bank for authorisation. Only authorised parties, such as the merchant and bank, can link the token back to the original data in the vault.
-
Completion of Transaction: Once the transaction is approved, the token can be stored for future use, such as for recurring subscriptions or one-click checkouts, eliminating the need for customers to re-enter their details.
What’s crucial here is that even if a hacker intercepts the token, it holds no value without access to the tokenisation vault or decryption methods. This is why tokenisation is a superior security method to traditional encryption methods.
Two types of tokenization payment
With Celeris, merchants can use two main types of tokenisation for payments:
Payment with CVV: If a user opts to “save card details” for a one-time transaction, their card number, expiry date, and name are tokenised and stored in the celeris token vault. For future purchases, the customer only needs to enter their CVV to complete the payment, creating a frictionless checkout experience.
Payment without CVV: For recurring billing, Celeris securely transmits card information to the issuer bank, which generates a unique ID for that card. This ID is stored and used for future recurring payments without requiring the customer to re-enter their CVV or other details, ensuring a seamless and secure subscription experience.
An Example of tokenization
Imagine you’re buying a pair of shoes online and you entered your credit card details, but before storing the sensitive credit card details, data protection technology (tokenisation) will replace the data with a randomly generated string of numbers or characters called “tokens” like “A1B2C3.” Even if hackers can breach the merchants’ side, this token cannot be used outside of that purchase, keeping your details safe and secure.
Tokenization vs. Encryption: A Detailed Comparison
-
Tokens are non-sensitive, which means even if a hacker breaches, he won’t expose cardholder details.
-
Unlike encryption, tokens cannot be mathematically reversed without access to a secure vault.
Traditional payment methods store data like credit card numbers in plaintext or encrypted formats, prime targets for cybercriminals. With tokenization, this data is stored as a form of a tokenized version (like 123456XYZ789), ensuring that even if a hacker intercepts the token, it’s useless for them without access to a secure vault provided by a payment gateway (like Celeris). By doing so, businesses can reduce the risk of breaches while maintaining seamless payment processing.